Attention all cloud enthusiasts! We’ll be diving into the world of Artificial Intelligence and Machine Learning, and how they’re helping to keep our data safe from cyber-criminals and other digital troublemakers. But first, let’s take a moment to appreciate the sheer hilarity of the phrase “cloud security“. I mean, who knew that a fluffy white mass floating in the sky would require so much security? Maybe next we’ll hear about “raindrop encryption” or “hurricane firewalls”.
But I digress… Let’s get down to business and explore the fascinating ways in which AI and ML are taking cloud security to the next level.

In this article, we’ll explore how AI and ML can be leveraged to shift from Reactive to Proactive cloud data security, and the benefits this can bring to businesses of all kinds.
The Growing Importance of Proactive Security Measures for Cloud Security
As more businesses adopt cloud-based technologies, the need for robust security measures to protect sensitive data is becoming increasingly crucial. Traditional reactive security measures that rely on identifying and responding to security incidents after they occur are no longer sufficient in today’s modern threat landscape.
- 61% of enterprises say they cannot detect breach attempts today without the use of AI technologies.
- 80% of telecommunications executives stated that they believe their organization would not be able to respond to cyberattacks without AI.
This is where proactive cloud data security comes into play. Proactive security measures use advanced technologies such as AI and ML to identify potential security threats before they occur, allowing for a more effective and efficient approach to cloud security. By taking a proactive approach:
- Businesses gain better control over their cloud security.
- Reduce the risk of cyber-attacks and data breaches.
- Protect their critical assets.
AI and ML to Predict and Prevent Cloud Security Breaches
AI and ML are powerful technologies that have revolutionized the field of cloud security. These technologies:
- Analyze vast amounts of data in real time, detect patterns, and identify potential security threats before they occur.
- Can be trained to detect unusual activity, identify network anomalies, and flag potential security threats, thereby predicting and preventing security breaches.
- Continuously learn from new data and improve their predictive capabilities over time, making them ideal for dynamic cloud environments.
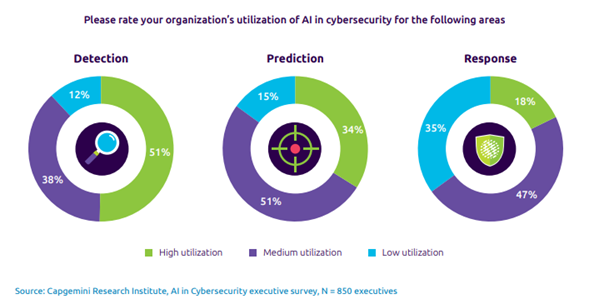
By leveraging AI and ML for predictive security, businesses gain a proactive approach to cloud security, enabling them to prevent potential security incidents before they occur. This helps organizations to reduce the risk of data breaches, minimize the impact of cyber-attacks, and ultimately protect their critical assets.
1. Identify Potential Security Threats Before They Occur
AI and ML algorithms can:
- Monitor user activity, network traffic, and system logs to detect anomalous behavior that may indicate a security breach, such as unauthorized access or data exfiltration.
- Provide proactive alerts to security teams, enabling them to take corrective action before a security incident occurs.
- Conduct threat-hunting exercises, which involve proactively searching for potential threats and vulnerabilities in the cloud environment.
AI and ML algorithms can identify patterns and trends that may indicate a security threat and alert security teams to potential risks. This can help organizations to stay one step ahead of potential hazards and minimize the impact of security incidents on their business.
2. Predictive Risk Management to Identify Potential risks and Prioritize Security Measures
Predictive Risk Management is a proactive approach to identify and address potential security risks before they become a reality. By leveraging predictive analytics, businesses can identify potential threats and vulnerabilities in their cloud environment and prioritize security measures accordingly.
Predictive analytics identifies critical assets, such as sensitive data or systems, and assesses the risk associated with each asset. Based on this risk assessment, security measures can be prioritized to protect these critical assets from potential security threats.
Moreover, predictive analytics identifies potential vulnerabilities in the cloud environment and prioritizes security measures to address these vulnerabilities. For example, suppose a vulnerability is detected in a software application. In that case, predictive analytics can assess the likelihood and impact of a potential exploit and prioritize security measures to address this vulnerability.
3. Real-Time Threat Detection to Prevent Security Incidents
Real-time threat detection is a crucial component of a proactive cloud security strategy. It involves continuously monitoring cloud environments for potential security threats and immediately responding to any identified threat to prevent a security incident from occurring.
By responding quickly to potential security threats, organizations can prevent the threats from turning into full-scale security incidents. Real-time threat detection can also help organizations minimize the impact of security incidents, such as data breaches, by quickly identifying the source of the breach and mitigating the damage.
Overall, real-time threat detection enables organizations to detect and respond to potential security threats in real time, ultimately reducing the risk of data breaches and other security incidents.
4. Automation to Streamline Security Operations and Improve Response Times
Automation and security orchestration are critical components of an effective and efficient cloud security strategy. These technologies enable organizations to:
- Streamline their security operations.
- Reduce the workload on security teams.
- Improve response times to potential security incidents.
Security Automation: This involves using software tools and technologies to perform routine security tasks automatically, such as vulnerability scanning or log analysis. This frees security teams to focus on complex functions like threat hunting or incident response. Automation also helps to eliminate human error, which can often be a source of security vulnerabilities.
Security orchestration: This process involves integrating and automating different security technologies and tools to create a more cohesive and effective security posture. Security orchestration can automate the incident response process by automatically triggering security tools to respond to a security incident. This can include isolating affected systems or disabling user accounts to prevent further damage.
Overall, automation and security orchestration are essential components of a modern cloud security strategy, enabling organizations to streamline their security operations, improve response times, and create a more comprehensive and effective security posture.
Addressing Cloud-Specific Security Challenges with AI/ML
Cloud environments present unique security challenges not encountered in traditional on-premises environments. These challenges include:
- Multi-tenancy
- Shared responsibility models
- Complex network architectures.
AI and ML technologies can help organizations overcome these challenges by:
- Providing enhanced visibility and control over cloud environments
- Automating critical security tasks
- Detecting anomalous behavior and unauthorized access.
- Identifying potential vulnerabilities and misconfigurations
Furthermore, AI and ML can be used to automate key security tasks, such as log analysis and vulnerability scanning, freeing up security teams to focus on more complex tasks. Automation can also help to eliminate human error, which can be a significant source of security vulnerabilities.
Overall, the unique security challenges presented by cloud environments require a proactive and sophisticated security strategy. AI and ML technologies can address these challenges by providing enhanced visibility and control, automating essential security tasks, and providing real-time threat intelligence.
The Future of Predictive Cloud Data Security
The future of predictive cloud data security is rapidly evolving, driven by emerging trends and technologies in the security space.
- Increasing use of Cloud-native Security Solutions: These are specifically designed to address the unique security challenges of cloud environments. These solutions leverage AI and ML to provide enhanced visibility and control over cloud environments and to automate key security tasks.
- Use of Container Security: This involves securing the individual containers that makeup cloud applications. Container security solutions use AI and ML to detect and respond to real-time security incidents, helping prevent data breaches and other security incidents.
- Edge Computing: This involves processing data at the edge of the network rather than in the cloud. This can help reduce cloud environments’ attack surface and improve overall security.
Wrap-Up
Prepare to embark on an exhilarating journey into the future of cloud data security! As organizations navigate the ever-evolving landscape of cloud environments, a host of groundbreaking solutions and technologies are emerging to tackle the unique security challenges they face. As we gaze into the future, the brilliance of predictive cloud data security shines brightly.
MSys Technologies is a leader in cloud security services powered by the cutting-edge forces of AI and ML! With a relentless pursuit of excellence, MSys Technologies unleashes the full potential of these transformative technologies, creating an unstoppable fortress of protection for organizations venturing into the cloud. Harnessing the power of AI and ML, MSys Technologies delivers unparalleled visibility, control, and automation, ensuring that every corner of the cloud environment is safeguarded against threats. MSys Technologies propels organizations towards a future where security becomes synonymous with invincibility, from detecting and neutralizing anomalies with lightning speed to providing real-time threat intelligence.
Connect with us now, to venture forth and seize the exciting opportunities that lie ahead. The frontier of cloud data security awaits your triumphant arrival!
